Is your WordPress blog safe from assaulters? It truly depends on how long it's been given that you upgraded your version of WordPress. It appears that the increasing popularity of the WordPress platform has increased the variety of security risks. Hackers have actually found a hole or 2 in older WordPress versions and are penetrating blogs that are working on old versions of WordPress.
PC Backup software application is a need to if you value your data - whether it be valuable household photographs or you organization accounts. The main reason for this is no matter how new your hardisk is, it will eventually fail. If it is new it is less most likely, however if it is a couple of years of ages the opportunities are increased - however even a brand-new hardisk can become what is sometimes termed an "early life failure". It is also a good idea since If the difficult drive fails, you will lose whatever. Your information may be retrievable, however expert business charge countless dollars for this service. By making backups you are conserving yourself cash and tension. Excellent PC backup software application will automate the procedure, once it is established. You pick which information goes where, and how typically this takes place.
7) What are their law enforcement and medical contacts? By being in direct contact with the authorities, a security business will be able to dispatch assistance immediately, specifically in the case of a frightening health emergency situation.

Home invasions, a minimum of in my neck of the woods, Colorado Springs, are the outcome of drug deals gone bad. They are severe criminal activities. The perps get what they desire by intimidation, risks and violence.
If you manage Cybersecurity Threats a WordPress site there is another thing to consider, having numerous websites on the same server can be harmful if they're not all well tended to. Believe of it by doing this, if one website gets an infection and they're all sitting beside each other, what do you believe will happen to the rest? Be careful how you manage several websites.
In all the research that I've done on break-in and home invasions I have found that 60% of all burglaries happened through unlocked windows and doors. And a remarkably big number of home intrusions take place right through the front door. Many people, particularly older people like myself just reflexively open the door when somebody rings the bell or knocks on it. NOT an excellent concept!!
There are a variety of different spray patterns that are utilized in self cybersecurity regulations defense sprays. These consist of stream, fog, cone, and foam. Each has its place and benefits. The stream sprays can be used at ranges of approximately 20 ft. This however needs fantastic precision and has a lower success rate.
Just thoroughly follow the 5 tips above and you can expect exceptional results in keeping your pc safe and secure and well preserved. Visit our site for more in depth guidance and limitless software tips and reviews. You will then take pleasure in each of the fruits, benefits and delights thereof. Finest get ready for even worse outcomes than those you might otherwise accomplish if you overlook them.
Evaluation Of 3 Of The Top Virus Scan Programs
If you can not access sites all of an unexpected, It is one sign that you may have the Security Tool set up in your computer. Other signs that you might have it, is the unexpected sluggishness in your computers operation or icons that appear to mysteriously appear without you doing anything and numerous other indications.
On top of a glare-proof screen, a wide and smooth display is another dream function. Preferably, the screen must be at least seven inches. If the screen is smaller than 7 inches, it would be difficult Cybersecurity Threats to search the web and play video games.
And just precisely why is this a great concept? If you have more than one PC or laptop you can merely move the external hard disk drive and connect it as much as the next PC - they are all USB compatible, in some cases SATA as well. Exist more reasons? If need be, an external difficult drive can be removed and put in a safe. Some are even fire-resistant.
This virus began as simple appear advertisements that would appear on your screen. As a growing number of ads were displayed, your computer system would be decreased in a huge method. Lots of would get so frustrated, they would discard their computer and buy a new one. Obviously there are programs like Spybot that will get rid of these from your computer system - if you understand enough to run the program. Nowadays, this infection is a huge money maker because every time an ad is shown on your maker, the individual established the adware earns money.
DO NOT DO IT. This is understood as the Windows Security Center Scam. It is actually an infection that enters your computer system and posts warnings that look like they originated from the genuine Windows Security Center program.
Once it remains in your system it would set up and configure itself so that it would run automatically as you boot and log on. It would then carry out a scan of your maker and later produce results that your computer is infected. It will make it possible for annoying pop-ups to install its full version for an amount of cash to be able to get cybersecurity threats rid of the infection.
And don't depend on a "safety" plugin to keep you safe. The finest line of defense is a good offense and the very best thing you can do is to keep up with your WordPress upgrades.
Upgrading Wordpress And Why It's So Critical
Before you do anything, look out! You might succumb to a trap. Web users all over the world have actually been reporting this Windows Security Center Warning. A pop up box that states something like, "Possible spyware infection detected". It recommends that you upgrade to a specific anti-spyware program in order to remove the threat.

One business I know had a problem with missing laptop computers. They encouraged the guards to inspect everyone with a laptop to see if they had approval to remove it from the structure. After a week, the guards unwinded on their tasks. The owner then had somebody enter the building, pack up all the laptops on one floor and hide them inside the structure. When the guards examined the flooring, they saw all the laptop computers were gone. The owner then recommended he was the one whom hid the laptops to prove a point. After that occasion, there disappeared missing laptops. Often you need to frighten the guards into doing their job.
Among the leading software application tools for spyware or adware elimination of AdSpyware Removal is XoftSpySE. This is offered at $29.95, along with a money back ensure for 56 days. This tool is ideal for Windows XP and Vista. You will have the ability to safeguard the security and efficiency of your operating system through this tool. On the other hand, noadware is also great for the operating systems Vista and Windows XP. It is simple to set up, and its performance is powerful and fast. Like the former software tool, you can download it at $29.95. It is also supplied with a 56-day money Cybersecurity Threats back warranty. The 2 other spyware adware removal software tools of the website which are proper for Windows XP and Vista are adwarealert and spywareremover. The previous is offered at $29, while the latter at $26.
Have you carried out a RF video sweep for concealed cams. Visitor's and trainees can set up concealed camera inside your school and find out when you go into a location. Some trainees set up or perhaps use concealed cams to tape-record unlawful images of women undressing. Do the sweep, you may be surprised at what you discover.
Being a double edged click here sword the Olympics could produce a lot of money or send us plummeting into financial obligation. More likely financial obligation viewing as we are currently in a cash scenario. Taking this threat would be a huge downside for the individuals. The HIGH opportunities that the the Olympics do trigger a cash issue you, individuals will be paying to clean everything up!
Finally some individuals see self defense sprays as something that ought to just be used by ladies and the senior. This is a foolish macho idea that is promoted by individuals who aren't dealing with major hazards regularly.
People simply assume that because they are obese their self-discipline must be dreadful. You may be surprised to discover your determination is actually respectable.
For running systems Windows XP down to Windows 98, the spyware or adware elimination software tools which are proper for them include adwarebot, spywarenuker, and spynomore. The first software application tool is provided to you at $24.95, together with a free trial variation and scanning. It also has a 56-day money back guarantee, like the remainder of the software tools of AdSpyware Elimination. On the other hand, AdwareBOT has been getting much popularity. It has brand-new features and it has the ability to scan your computer system easily and rapidly. You can download this software at $39.95. The last software application tool among the premier tools of AdSpyware Removal is SpyNoMore. This can be used for workplace use at $29.95.
Home Security - How To Prevent A Home Intrusion - Top Tips
1) Where does the company stack up in terms of size? Larger is not constantly much better, but a larger business has options not available to little operations. For instance, the power of a business to react throughout regional blackouts. You will be able to bypass the unlikely if your security business has multiple command centers.

Single socket layer (SSL) security is just a file encryption tool that garbles data throughout transmission and figures out the garbled information upon receipt at your host server. If you're a business site, you need SSL file encryption coming and going.
One would typically obtain it through numerous ways. It could be through a suspicious website, complimentary scanning offers, hacked advertisements and so on. Either method, once it gets in to your computer it guarantees absolutely nothing however trouble.
Get a fire wall. Although Microsoft Windows has a fundamental firewall software, it is much better to get the finest available. Generally this feature is part and parcel of all the finest Internet Security Suites. A firewall program manages data traffic in between your PC and the internet. This is very important since hackers can't get in due to your PC being undetectable to the outside world. Since unauthorised programmes (or users) can't call the outside world by means of the internet, and in addition might be important.
Today, unlike years back, there are many kinds of individual safety and self protection gadgets offered. Personal alarms are small and healthy in any purse or pocket-- they even clip to your belt. These alarms emit an extremely loud sound that will get anybody's attention. Likewise, pepper spray comes in Cybersecurity Threats various camouflaged containers-- pagers, pens, essential chains and even lipstick!
Keep it infection complimentary. Why is this essential? Nothing degrades security and efficiency more than an infection or malware invasion. How are you affected whenever you follow this advice? By setting up one of the leading 5 anti-viruses software suites you are practically ensured to be safe against 99% of threats.
You must be seeing results pretty quickly if you are doing this whole list well. If not, go through the entire list and see more info if you missed out on anything or did something wrong.
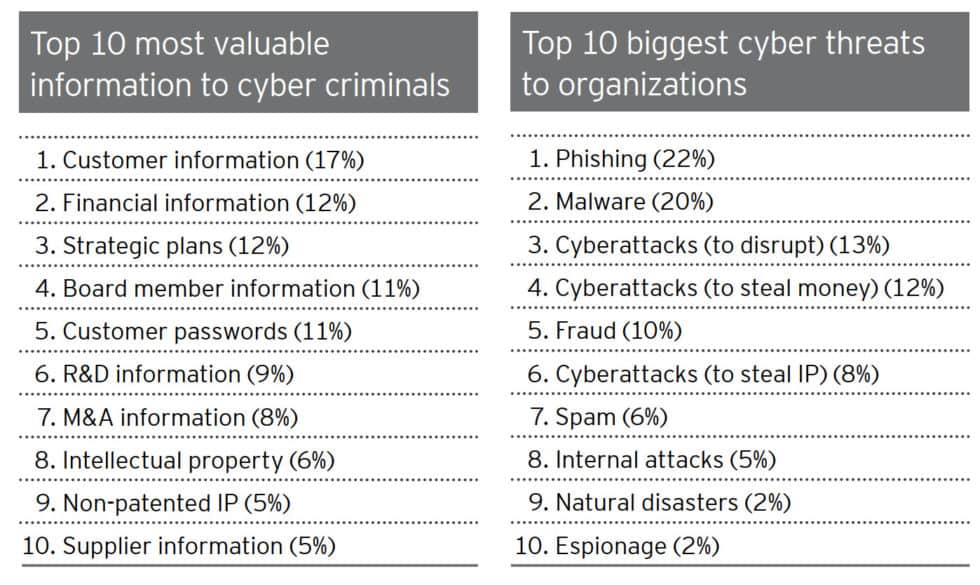
What cybersecurity regulations can protect businesses
Recent discoveries, such as the xz Utils backdoor, highlight dangers in our electronic infrastructure.
The invention of the internet is going to be regarded as a watershed point in history. It has had a profound effect on human civilisation. Originally developed as a patchwork of devices and networks connected through various ad hoc connections, the world wide web's decentralised nature allows it to operate. However, a cybersecurity expert lately found a hidden flaw in xz Utils, a lesser-known software crucial to the Linux systems that power most of the internet's servers worldwide. Had this flaw not been found in time, the harm could have been huge, potentially compromising anything from crucial commercial infrastructure to individuals' personal data. This event underscores a concerning trend: cyber threats are now with the capacity of attacking not only separated systems however the very backbone of our electronic world.
The current protection breach in xz Utils, which is an open-source program, reveals a substantial vulnerability. Open-source software enables anyone to see, change, and contribute to its codebase, just like how one might edit a write-up in an online encyclopedia. This openness encourages innovation but also presents safety challenges. As a lot more of our data and systems make the switch online, the possibility of cyber attacks increases, making vital sectors like healthcare, finance, government, utilities, and worldwide logistics prime targets for cybercriminals. Simply Take, for example, the healthcare sector; it confronts increased risks since it stores sensitive patient information, which may be exploited for fraudulence or unauthorised access. Likewise, complex supply chains are vulnerable to cyber threats, as business leaders like Sultan bin Sulayem of P&O may likely be aware of. These chains span many locations and include various stakeholders. This makes them at risk of attacks which could paralyse whole companies, as business leaders like Vincent Clerc of Maersk would probably suggest. A cyber incident at an important node, such as a major transportation hub, could halt operations, causing extensive interruption, as we have seen in the past few years.
Global supply chains usually rely on third-party vendors and logistics providers for their efficiency and specialisation, as business leaders like Rodolphe Saadé of CMA CGM may likely confirm this. But, this dependence introduces additional security risks, particularly if these 3rd parties do not have a robust cybersecurity measure in position. In response to these vulnerabilities, professionals argue that not all remedies are technical; some treatments are regulatory in nature, including the introduction of certification programs that demand organisations to demonstrate adherence to cybersecurity standards. People are relying more on technology in their daily lives, so it's becoming more and more essential to guard against cyber attacks. This growing focus on cybersecurity shows the necessity for a fresh way of the electronic landscape. Not merely should specific businesses strengthen their defences, but industry requirements additionally needs to evolve to keep up with the expanding and ever-changing nature of cyber threats.